Students can Download 2nd PUC Computer Science Previous Year Question Paper March 2017, Karnataka 2nd PUC Computer Science Model Question Papers with Answers helps you to revise the complete Karnataka State Board Syllabus and score more marks in your examinations.
Karnataka 2nd PUC Computer Science Previous Year Question Paper March 2017
Time: 3 Hrs 15 Min
Max. Marks: 100
PART – A
Answer all the following questions. Each question carries one mark. (10 × 1 = 10)
Question 1.
What is a bus?
Answer:
A bus is a set of wire connected between the units for the purpose of carry the signals between the units.
Question 2.
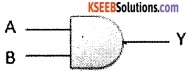
Write the standard symbol for AND gate.
Answer:
Question 3.
Define an array.
Answer:
Array is a collection of similar elements that share a common name. It is a structured data type and allocates memory contiguously.
Question 4.
Is it possible to access data outside a class?
Answer:
Yes, the public members can be accessed by member functions of the class and non member function (outside the class) of the class.
![]()
Question 5.
Mention any one advantage of pointer.
Answer:
The two advantages of the pointer are
- For objects memory can be allocated dynamically during runtime.
- When objects are not used, then memory can be released.
- Memory is efficiently used.
Question 6.
Define an entity.
Answer:
An entity is a person, place, thing or event for which data is collected and maintained.
Question 7.
What is chatting?
Answer:
It is online communication between two users through the computer. Once a chat has been initiated, either user can enter text by typing on the keyboard and the entered text will appear on the other user’s monitor.
Question 8.
What is a server?
Answer:
A server is a computer program that provides services to other computer programs and their users in the same or other computers.
OR
The computer that a server program runs in is also referred to as a server.
![]()
Question 9.
Expand WWW.
Answer:
Worldwide Web
Question 10.
What is a website?
Answer:
A website is a collection of web pages generally written using Hyper Text Markup Language.
PART -B
Answer any five questions. Each question carries two marks. (5 × 2 = 10)
Question 11.
Prove algebraically x + xy = x.
Answer:
LHS x + xy
= x + x x + y (distributive law)
= 1 1+y (absorption law)
= 1
Question 12.
State the principle of duality. Write the dual of 1 + x = 1.
Answer:
The principle of duality states that starting with a Boolean relation, another relation can be derived by
- Changing each OR sing (+) to an AND sign (.)
- Changing each AND sing (.) to an OR sign (+).
- Replacing each 0 by 1 and each 1 by 0.
- All variables are complemented.
For example, (X + Y’) dual is (X’. Y)
1 + X = 1 is 0 . X = X.
Question 13.
Define base class and derived class.
Answer:
1. base class:
A base class is a class from which other classes are derived.
2. derived class:
The class that inherits is called derived class.
The inheriting class is called the derived class.
![]()
Question 14.
Write the features of default constructors.
Answer:
The features of default constructors are:
- All objects of a class are initialized to same set of values.
- These constructors has no arguments.
- These constructors are automatically called when every object is created.
Question 15.
Differentiate between read() and write().
Answer:
| read() | write() |
| belongs to the class ifstream | belongs to the class ofstream |
| used to read binary data from a file | used to write binary data to a file |
| Syntax: fin.read( (char *) &variable, sizeof(variable)); | Syntax: fout.write( (char *) &variable, sizeof(variable)); |
Question 16.
Write the difference between data and information.
Answer:
Data:
1. Data is a collection of facts, figures or statistics. Data is transformed into meaningful information. It is raw material of information.
2. Information:
It is processed data with definite meaning. Information gives meaning.
![]()
Question 17.
Give the syntax and example of UPDATE command in SQL.
Answer:
UPDATE command:
It can be used to change row values from a table. The SET key word takes the column in which values needs to be changed or updated. The WHERE keyword is used to filter the records on some condition.
Syntax:
UPDATE tablename SET columnname = values WHERE Condition;
Example:
UPDATE student SET combn = ‘PCMCs’ where combn=’pcmc’;
Question 18.
What is communication (transmission) mode? Explain simplex mode.
Answer:
The communication mode is the technique of transmitting and receiving signals between the sender and receiver.
Simplex mode:
The communication occurs in one direction only. For example, radio receiver and radio transmitter.
PART – C
Answer any five questions. Each question carries three marks: (5 × 3 = 15)
Question 19.
Explain the characteristics of motherboard.
Answer:
The characteristics of motherboard identifies different kinds of motherboards, including Physical characteristics, which in combination are called the form factor like XT, AT Baby AT and ATX motherboard; The chipset used, which defines the capabilities of the motherboard such as an AMD, Intel, NVidia, SiS, or VIA chipset; The processors the motherboard supports; Different processors use different sockets or slots. Based on the type, there are two main types of slots.
a. Socket 7:
Is a 321-pin socket for Pentium class CPUs – Pentium MMX, K5, K6, etc.,
b. Slot 1:
Pentium ll/IH CPUs use slot 1.
The BIOS it uses – System BIOS is a chip located on all motherboards that contain instructions and set up for how your system should boot and how it operates. The phoenix and AMI are the two BIOS manufacturers and the internal and expansion buses that it supports.
Question 20.
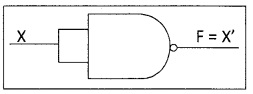
Realize AND, OR, NOT gates using NAND gates.
Answer:
1. Implementing AND using NAND gates:
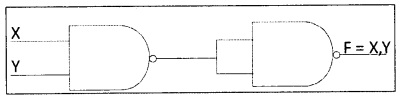
2. Implementing OR using NAND gates:
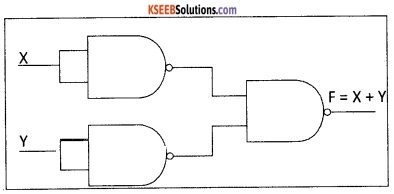
3. Implementing NOT using NAND gates:
![]()
Question 21.
Explain the memory representation of two dimensional array.
Answer:
Let A be two-dimensional array
Let M is rows and N is columns
The A array may be stored in the memory in one of the following methods;
1. Row-major representation:
In this type of method, the first row occupies the first set of memory locations reserved for the array and second-row occupies the next set and so on.
2. Column-major representation:
In this type of method, the first column occupies the first set of memory locations reserved for the array and the second column occupies the next set and so on.
Question 22. Define:
- Pointer
- Static memory allocation
- Dynamic memory allocation
Answer:
- A pointer is a variable that holds the memory address, usually the location of another variable.
- The fixed size of memory allocation and cannot be altered during runtime is called static memory allocation.
- Allocation of memory at the time of execution (run time) is known as dynamic memory allocation.
Question 23.
Explain any three modes to open a file in C++.
Answer:
The file can be opened both for input and output operations using fstream class.
The syntax for opening a file with constructor is fstream object(“filename”, mode);
The syntax for opening a file with open() is fstream object.open(“filename”, mode);
Therefore, file can be opened using different modes. They are
ios::in opens file for reading only. For example, fstream fin(“te’xt.dat”, ios::in);
ios::out opens file for writing only. For example, fstream fout(“text.dat”, ios::out);
ios::app opens a file to append to end of file. For example, fstream
file.open(“text.dat”,ios::app);
Question 24.
Mention database users.
Answer:
There are different types of database users. They are
1. Application programmers or Ordinary users:
These users write application programs to interact with the database. Application programs can be written in some programming language typically a SQL statement to DBMS.
2. End Users:
End users are the users, who use the applications developed. They just use the system to get their task done. End users are of two types:
- Direct users
- Indirect users.
3. Database Administrator (DBA):
Database Administrator (DBA) is the person which makes the strategic and policy decisions regarding the data of the enterprise, DBA is responsible for overall control of the system at a technical level.
4. System Analyst:
System Analyst determines the requirement of end-users, and develops specifications for transactions that meet these requirements. System Analyst plays a major role in database design, technical aspect, etc. of the system.
![]()
Question 25.
Give the services of e-commerce.
Answer:
Few services of eCommerce are:
- Domain name purchasing.
- Secure hosting.
- Full integration with the payment gateway of your choice.
- Web design.
- Shopping cart system.
- Marketing.
Question 26.
Explain any three HTML tags.
Answer:
1. The <p> tag is a paragraph tag.
Usage:
<p> HTML paragraphs </p>
2. The <table> tag is a table tag that creates a table in HTML.
Usage:
<table> </table>
3. The <tr> tag is a table row tag that creates a row in a table.
Usage: <tr> </tr>
PART – D
Answer any Seven of the following questions. Each question carries Five marks: (7 × 5 = 35)
Question 27.
Reduce F(A,B,C,D) = Σ(0,4,6,7,8,12,14,15) using K-map.
Answer:
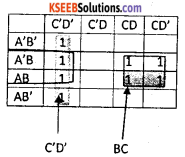
The F(A,B,C,D) = C’D’ + BC + BD’
Question 28.
Write an algorithm to insert an element in an array.
Answer:
A is an array
N is number of elements (size)
Element is a data element
Pos is the location of the element to be inserted.
Insertion (A, N, Element, Pos)
Step 1: for i = N-1 downto Pos repeat step 2
Step 2: A[i+1] = A[i]
End for
Step 3: A [Pos] = Element
Step 4: N = N + 1
Question 29.
What is a stack? Write an algorithm for PUSH() and POP() operations.
Answer:
Algorithm for PUSH operation:
PUSH(STACK, TOP, SIZE, ITEM)
Step 1: if TOP >= N-1 then
PRINT “stack is overflow”
Exit
End of if
Step 2: Top = TOP + 1
Step 3: STACK[TOP] = ITEM
Step 4: Return
Algorithm for POP operation:
PUSH(STACK, TOP, ITEM)
Step 1: if TOP = 0 then
PRINT “stack is empty”
Exit
End of if
Step 2: ITEM = STACK[POP]
Step 3: TOP = TOP -1
Step 4: Return
![]()
Question 30.
Write the applications of OOPs.
Answer:
Some of the real life applications of object oriented programming are given below;
- Computer graphic applications.
- CAD/CAM software.
- Object oriented database.
- User interface design such as windows.
- Real time systems.
- Simulation and modeling.
- Artificial intelligence and expert systems.
Question 31.
Explain class definition with syntax and example.
Answer:
A class is a structured data type in C++ which is a collection of variables and functions. A class in C++ combines related data and functions together. It makes a data type which is used for creating objects of this type
The syntax of a class definition:
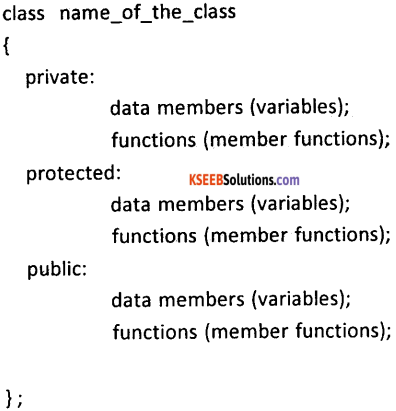
Question 32.
Explain inline function with programming example.
Answer:
Declaration and Definition of inline function
sinline returntype_specifier functioname (arguments)
{
….
}
The definition of inline function should be defined before all functions that call it.
The function definition should have the prefix inline.
Example:

![]()
Question 33.
What is a destructor? Write its syntax and example.
Answer:
It is a special function used to release the memory space allocated by the object.
→ Name of the Destructor is similar to the class, which it belongs.
→ It does not have argument(s) and doesn’t return any value (no return type)
→ Destructor is preceded by ~ (tilde) sign.
Following points should be kept in mind while defining and writing the syntax for the destructor:
- A destructor function must be declared with the same name as that of the class to which it belongs.
- The first character of the destructor name must begin with a tilde (~).
- A destructor function is declared with no return types specified (not even void).
- A destructor function must have public access in the class declaration.
General Syntax of Destructors:
~ classname();
The above is the general syntax of a destructor. In the above, the symbol tilde ~ represents a destructor which precedes the name of the class.
For example,
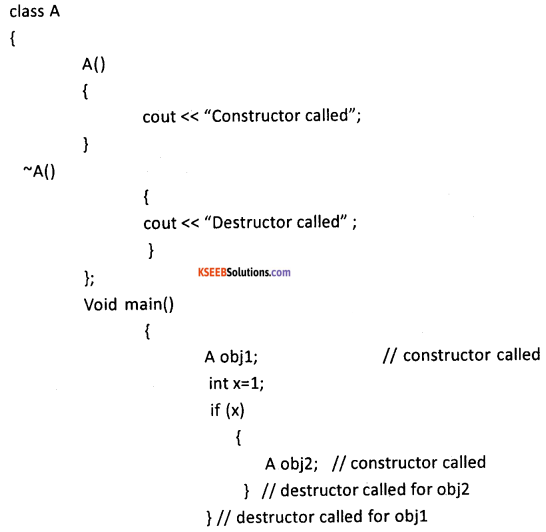
Question 34.
Write the types of inheritance. Explain any two.
Answer:
The different types of inheritance are single inheritance, multilevel inheritance, hierarchical inheritance, multiple inheritance and hybrid inheritance.
1. Single inheritance:
A derived class with only one base class is called single inheritance. For example, If A is base class then class B derive from base class A.
2. Multilevel inheritance:
A class can be derived from another derived class which is known as multilevel inheritance. For example, The derived class C inherit B class whereas B is derived from class A.
![]()
Question 35.
Briefly explain the data processing cycle.
Answer:
DATA PROCESSING CYCLE:
Data processing is the activity of collecting the data from various sources, properly organizing and processing to obtain required information.
The stages of data processing cycle
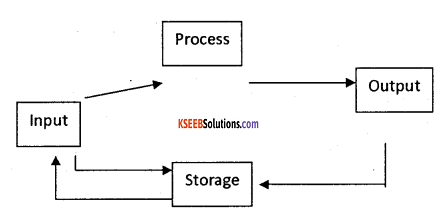
a. Data collection:
Data required for an organization may be available at various places. It involves identifying the source of data for collection. The sources may include documents, such as invoices, sales orders, purchase orders etc., for the purpose of processing.
b. Data input:
The gathered/collected data is entered into the system in the suitable format which is acceptable by the data processing system for the necessary process.
c. Processing of data:
Before any process is applied, classifying the data or grouping the similar type of data is performed. Then to such data proper arrangement/order is done i.e., in ascending or in descending order. Then verification for any missing data, incomplete data is done. Finally calculation process gives the information.
d. Data output:
It is necessary to put the results in proper format in the form of a summarized report, consolidated report, statements etc.,
e. Data storage:
The inputted data and generated results are stored for the future use. They are stored using different mass storage devices (Hard disk, floppy dis, etc.,).
Question 36.
Write the purpose of the following SQL function:
- count()
- max()
- min()
- avg()
- sum()
Answer:
The built-in functions associated with GROUP functions in SQL are
1. COUNT function- returns the count of records that satisfies the condition for each group of records.
Example:
SELECT department, COUNT(*)FROM employees WHERE salary > 25000 GROUP BY department;
2. MAX function- returns the maximum values from the column for each group of records.
Example:
SELECT department, MAX(salary) FROM employees GROUP BY department;
3. MIN function – returns the lowest values from the column for each group of records.
Example:
SELECT department, MIN(salary)FROM employees GROUP BY department;
4. AVG function – returns the average values from the column for each group of records.
Example:
SELECT AVG(cost) FROM products WHERE category = ‘Clothing’;
5. SUM function- returns the total values from the column for each group of records.
Example:
SELECT department, SUM(sales)FROM order_details GROUP BY department;
![]()
Question 37.
Give the measures of preventing virus.
Answer:
The different measures for preventing virus are
1. Install quality antivirus:
The users should install professional, business-grade antivirus software on their PCs. Pro-grade antivirus programs update more frequently throughout the, protect against a wider range of threats (such as rootkits), and enable additional protective features (such as custom scans).
2. Install real-time anti-spyware protection:
Use of professional (or fully paid and licensed) anti-spyware programs are required to prevent infections and fully remove those infections already present.
3. Keep anti-malware applications current:
Antivirus and anti-spyware programs require regular signature and database updates. Without these critical updates, anti-malware programs are unable to protect PCs from the latest threats. Computer users must keep their antivirus and anti-spyware applications up to date.
4. Perform daily scans:
Enabling complete, daily scans of a system’s on hard drive gives protection. These daily scans can be invaluable in detecting, isolating, and removing infections that initially escape security software’s attention.
5. Disable autorun:
Many viruses work by attaching themselves to a drive and automatically installing themselves. As a result, connecting any network drives, external hard disks, or even thumb drives to a system can result in the automatic propagation of such threats. The users can disable the Windows autorun feature to avoid.
6. Don’t click on email links or attachments:
Users should never click on email attachments without at least first scanning them for viruses using a business-class anti-malware application. As for clicking on links, users should access Web sites by opening a browser and manually navigating to the sites.
7. Use a hardware-based firewall:
The software-based firewall included with Windows isn’t sufficient to protect systems. For this reason, all PCs connected to the Internet should be secured behind a capable hardware-based firewall.